Cloudera Navigator Data Encryption Overview
 Warning: Encryption transforms coherent data into random, unrecognizable information for
unauthorized users. It is absolutely critical that you follow the documented procedures for encrypting and decrypting data, and that you regularly back up the encryption keys
and configuration files. Failure to do so can result in irretrievable data loss. See Backing Up and Restoring Key Trustee Server and
Clients for more information.
Warning: Encryption transforms coherent data into random, unrecognizable information for
unauthorized users. It is absolutely critical that you follow the documented procedures for encrypting and decrypting data, and that you regularly back up the encryption keys
and configuration files. Failure to do so can result in irretrievable data loss. See Backing Up and Restoring Key Trustee Server and
Clients for more information.
Do not attempt to perform any operations that you do not understand. If you have any questions about a procedure, contact Cloudera Support before proceeding.
- Cloudera Navigator Key Trustee Server
Key Trustee Server is an enterprise-grade virtual safe-deposit box that stores and manages cryptographic keys. With Key Trustee Server, encryption keys are separated from the encrypted data, ensuring that sensitive data is protected in the event that unauthorized users gain access to the storage media.
- Cloudera Navigator Key HSM
Key HSM is a service that allows Key Trustee Server to integrate with a hardware security module (HSM). Key HSM enables Key Trustee Server to use an HSM as the root of trust for cryptographic keys, taking advantage of Key Trustee Server’s policy-based key and security asset management capabilities while satisfying existing internal security requirements regarding treatment of cryptographic materials.
- Cloudera Navigator Encrypt
Navigator Encrypt is a client-side service that transparently encrypts data at rest without requiring changes to your applications and with minimal performance lag in the encryption or decryption process. Advanced key management with Key Trustee Server and process-based access controls in Navigator Encrypt enable organizations to meet compliance regulations and ensure unauthorized parties or malicious actors never gain access to encrypted data.
- Key Trustee KMS
For HDFS Transparent Encryption, Cloudera provides Key Trustee KMS, a customized Keystores and the Hadoop Key Management Server that uses Key Trustee Server for robust and scalable encryption key storage and management instead of the file-based Java KeyStore used by the default Hadoop KMS.
- High-performance transparent data encryption for files, databases, and applications running on Linux
- Separation of cryptographic keys from encrypted data
- Centralized management of cryptographic keys
- Integration with hardware security modules (HSMs) from Thales and SafeNet
- Support for Intel AES-NI cryptographic accelerator for enhanced performance in the encryption and decryption process
- Process-Based Access Controls
- Databases
- Log files
- Temporary files
- Spill files
- HDFS data
- HDFS data
- Local filesystem data
| Data Type | Data Location | Key Management | Additional Services Required |
|---|---|---|---|
| HDFS | HDFS | Key Trustee Server | Key Trustee KMS |
Metadata databases, including:
|
Local filesystem | Key Trustee Server | Navigator Encrypt |
Temp/spill files for CDH components with native encryption:
|
Local filesystem | N/A (temporary keys are stored in memory only) | None (enable native temp/spill encryption for each component) |
Temp/spill files for CDH components without native encryption:
|
Local filesystem | Key Trustee Server | Navigator Encrypt |
| Log files | Local filesystem | Key Trustee Server | Navigator Encrypt
Log Redaction |
For instructions on using Navigator Encrypt to secure local filesystem data, see Cloudera Navigator Encrypt.
Cloudera Navigator Encryption Architecture
The following diagram illustrates how the Cloudera Navigator encryption components interact with each other:
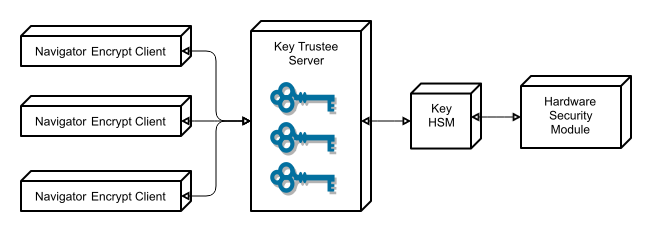
Key Trustee clients include Navigator Encrypt and Key Trustee KMS. Encryption keys are created by the client and stored in Key Trustee Server.
Cloudera Navigator Encryption Integration with an EDH
The following diagram illustrates how the Cloudera Navigator encryption components integrate with an Enterprise Data Hub (EDH):
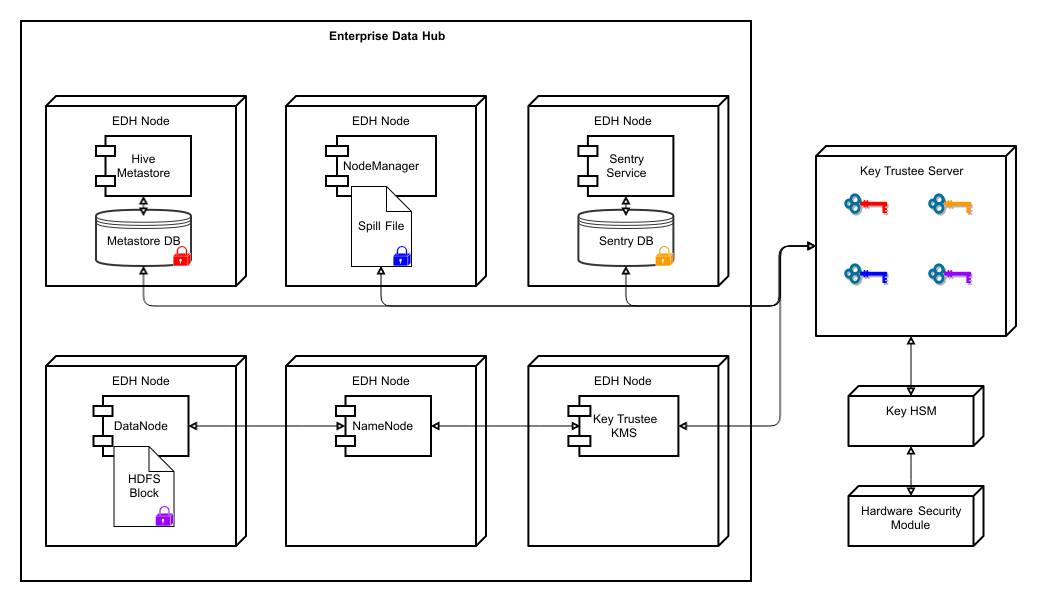
For more details on the individual components of Cloudera Navigator encryption, continue reading:
| << Cloudera Navigator Data Management Overview | ©2016 Cloudera, Inc. All rights reserved | Cloudera Navigator Key Trustee Server Overview >> |
| Terms and Conditions Privacy Policy |