TLS and Kerberos Configuration for Cloudera Manager High Availability
This section contains information about configuring Cloudera Manager for high availability when TLS is enabled.
Configuring TLS for Cloudera Manager High Availability
For information about on setting up TLS security with Cloudera Manager, see t Configuring TLS Security for Cloudera Manager.
- When creating a certificate for the Cloudera Manager Server, make sure that you use the load balancer FQDN (CMSHostname, as described in the TLS configuration document referenced above) as your CN.
- Make sure that the same keystore and truststore are placed at the same locations on both CMS1 and CMS2 (or share those locations through a shared network mount on both CMS1 and CMS2).
- After completing the steps in the TLS configuration document referenced above, verify TLS/SSL access by accessing the Cloudera Management Admin Console in a web browser, using the load
balancer URL:
https://[CMSHostname]:[TLS_Port]
- For agent configuration of the Cloudera Management Service hosts:
-
If your agents are configured to authenticate the Cloudera Manager Server, Cloudera recommends sharing the filepath (or copying the files manually) for the verify_cert_file option as specified in /etc/cloudera-scm-agent/config.ini between MGMT1 and MGMT2. If, however, you are using the verify_cert_dir mechanism, the verify_cert_dir directory contains symlinks when configured correctly with c_rehash. Cloudera recommends regenerating that directory based on actual certificate references on both the primary and secondary hosts.
-
If your cluster uses TLS authentication of agents to Cloudera Manager (see Level 3: Configuring TLS Authentication of Agents to the Cloudera Manager Server), share the certificate and keys specified over NFS or by copying them to the same locations on both MGMT1 and MGMT2.
-
 Note: Remember to restart cloudera-scm-agent after making changes to
these files or configuration options.
Note: Remember to restart cloudera-scm-agent after making changes to
these files or configuration options.Configuring Kerberos Authentication for Cloudera Manager
- If you have configured CMS1 to store Cloudera Manager Server KDC access credentials at /etc/cloudera-scm-server, they must be mirrored on to the same location on CMS2.
- Install Kerberos client libraries on both CMS1 and CMS2, and configure the /etc/krb5.conf file identically on both machines.
- Make sure that /etc/krb5.conf has been configured and distributed on both MGMT1 and MGMT2 hosts.
- If you add the Cloudera Management Service to an existing installation using Kerberos authentication (as you do in the Installing the Primary procedure), your Cloudera Management Service could fail to start and displays following message:
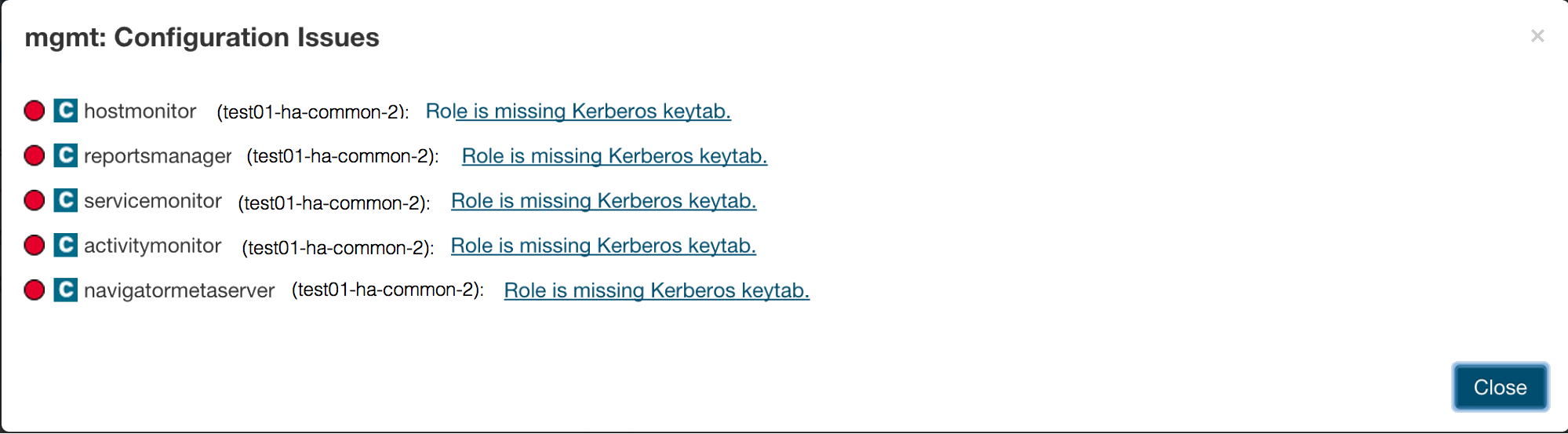
This message is expected, and can be corrected by generating Kerberos credentials for these roles using the Cloudera Manager Admin Console. Select .
For additional instructions on configuring Kerberos authentication for Cloudera Manager, see Configuring Authentication in Cloudera Manager.
| << Database High Availability Configuration | ©2016 Cloudera, Inc. All rights reserved | Backup and Disaster Recovery >> |
| Terms and Conditions Privacy Policy |